Content
How to Ensure Magento 2 Security
Magento security is among the key aspects to look out for in the modern world of eCommerce. A commercial nature makes a large number of sites powered by this platform an attractive target for all kinds of illegal actions (phishing, database hacking, theft of private and payment data as well as of financial resources, etc.).
Lets talk about itHave a project in mind?
When a commercial site is hacked, many negative consequences for both buyers and vendors arise. The former lose money and time while the latter are confronted with a loss of reputation, profit, concessional lending conditions in court proceedings, and tightening of control over financial bodies. To avoid all these issues, consider the basic methods of Magento 2 security best practices.
Also read:
Magento Ecommerce Development Guide
How to Build A Multi Vendor Marketplace
The Benefits of Magento Custom Module Development

Image Source: www.inc.com
Conduct a Regular Magento Security Audit
Attracting experienced professionals will certainly provide faster, more thorough identification of resource errors. In cases where this is not possible for financial or labor reasons, the company can conduct a Magento test for security on its own.
Magento Security Checklist
Below is a list of priority measures that can be carried out independently or with the help of professional developers.
- Use Magento Security Scan to monitor your store security.
- Update security patches.
- Check reliability of the user authentication procedure.
- Ensure confidential files storing protection.
- Check the state of antivirus databases.
- Disable non-protected PHP commands (protection of unauthorized connections).
- Enable restricted access to the local.xml file.
- Conduct systematic checks of the server’s action log to identify malicious actions.
- Check third-party tools for vulnerabilities.
Is Magento secure in a major way as a platform? There is no perfection and hackers tend to find new ways to break into websites daily. Checking for regular updates and conduct audits are the basic way to stay careful and protected.
Learn more about: How to Hire the Best Magento Developers in 2021
Dinarys eCommerce experts can help you audit the code, check the security of the resource end-to-end, detect vulnerabilities, and solve major issues.
Top 10 Magento Security Best Practices
On top of all the mentioned-above preventive measures, here’s a more in-depth technical Magento security checklist.
1. Encryption of connections (SSL/HTTPS)
The main function of the SSL certificate is to encrypt data during transmission between servers and browsers. This method prevents unauthorized use of customer data, his/her credit card, access to the resource. Information is exchanged using an HTTPS connection, which reduces the risk of interception by third parties.
Data encryption is one of the key Magento security features that you should pay attention to. Google penalizes sites that do not use HTTPS by providing clear warnings to customers in the URL bar.
2. Use of FTP
SFTP (Secure File Transfer Protocol) is a protocol that provides secure access to the file system of a resource. Using this tool, you need to create a complex, preferably randomly generated password for it.
3. Admin access
Elaborating on the topic of passwords - to ensure sturdy Magento 2 security, you must use a combination of uppercase and lowercase letters, numbers, special characters, (%, ^, #). It is advisable to avoid real words, common usernames, and the use of a similar access code on other resources.
4. Two-factor authentication
A reliable username and a complex access code aren’t really enough when it comes to sufficient security. Hackers have a wide arsenal of malicious methods to gain access to the site (phishing, random password attempts, and such).
Two-factor authentication provides an additional layer of resource protection, including:
- limiting access to trusted devices only;
- generation of a new code that is sent to a mobile device upon each authorization attempt;
- limiting the number of failed authorization attempts.
5. Disabling directory indexing
Directory indexing is one of Magento 2 security features enabled on most resources. Disabling it is a necessary step to block access to your domain files. While online, the list of directory files can be accessed by anyone, which makes the resource vulnerable to attacks and hacks.
6. Website backups
Among the Magento 2 security best practices is the creation of backup copies of the resource. This helps to restore the previous versions of the site in the event of a failure or data loss. The problem can be caused by hacking the site, accidental or intentional deletion of data, errors due to incorrect configuration or new extensions.
Magento's default functionality lets you backup your system, database, and media. Depending on the need - copies can be downloadable and scheduled while stored on a hard drive or in the cloud.
7. Limiting backend access
Companies need to make sure that the availability of employee data is consistent with their tasks. The Magento 2.3 backend has the ability to assign roles. However, you should keep in mind that opening new accesses is not a quick process.
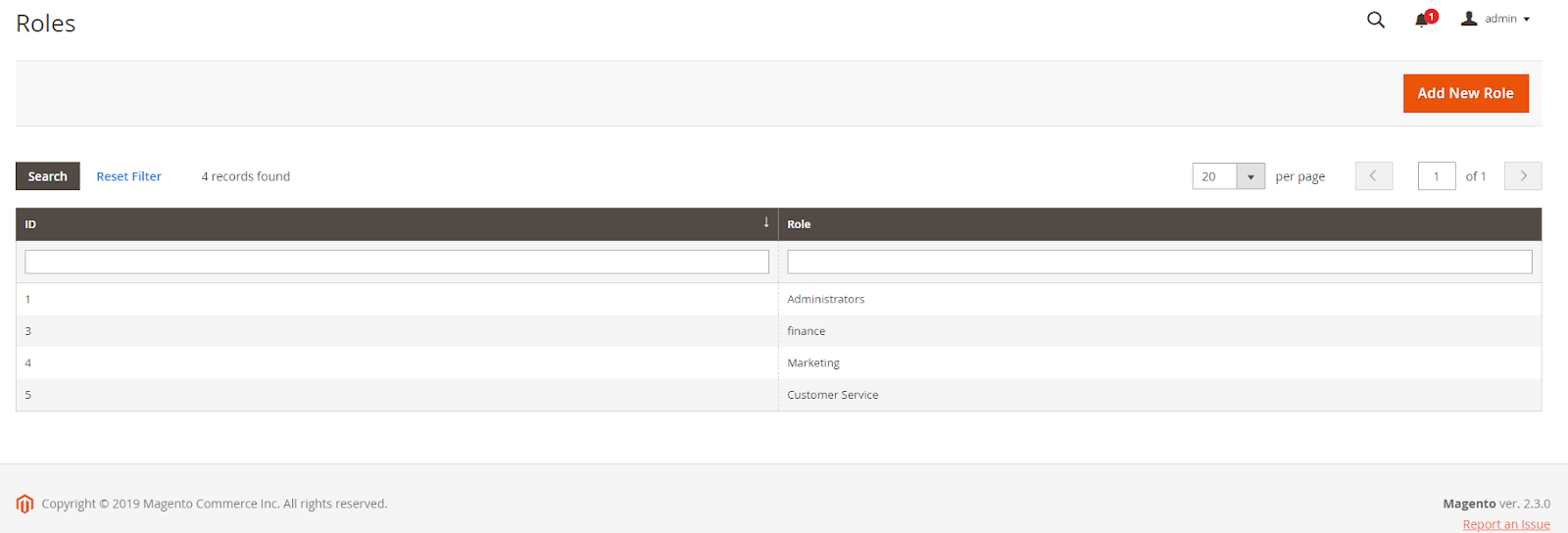
Image Source: Limiting backend access
8. Codebase management
After the final setting of the resource, it is recommended to monitor the Magento files. This allows for detecting new or changed objects. Ask the hosting to configure immediate email notifications to let responsible experts know about the changes made so they could quickly fix possible issues.
9. Provider reliability
The platform on which your resource is located should never be saved on. A shared hosting plan can reduce costs due to inexpensive options, but it is more susceptible to hacker attacks and contains more vulnerabilities prone to security breaches.
A dedicated resource supported by a reputable company with proactive security measures is a safer solution. If you need help finding a reliable hosting, contact our specialists right now. Our experience in developing sites on Magento, Shopware, and implementing custom resources will help you choose the optimal ratio of price, quality and security.
Know more: How to choose Ecommerce Web Hosting
10. MySQL injection protection
SQL injection is hacker’s favorite malicious method to capture sensitive data in databases. They access data using harmful SQL queries in various forms on the pages of your website.
Despite the fact that Magento has strong protection against such attacks, it is not always enough. You can use third-party firewalls (like NAXSI) will help to further protect the project from data leakage. The software filters the traffic exchanged with the database, preventing malicious SQL queries from entering it.
Conclusion
Securing an eCommerce resource is an integral part of doing business. Regardless of your company scale - the issue of data protection is simply essential. With the right approach, a business can win an audience as well as minimize issues of a different nature in the future.
Contact our team to get professional consulting or audit services.
Magento, like any other software platform, has its vulnerabilities. However, constant monitoring of activities, the operational implementation of preventive, ongoing security measures will help to lead business most painlessly and systematically.
Let professionals meet your challenge
Our certified specialists will find the most optimal solution for your business.



