Content
E-commerce Security: What E-merchants Should Know About Cyber Threats
Time to read: 20 minutes
Webscale believes that e-commerce merchants will have to spend 20% more on cybersecurity over the next 3 years. Such confidence is based on the distressing statistics regarding the emerging cyber threats in online shopping. The COVID-induced new normal of remote businesses has significantly boosted e-commerce activities. As a result, cybercriminals received another impetus to attack both e-stores and their visitors more intensively.
Investigators from NordLocker have found 1.2 terabytes of data stolen from about 3.2 million Windows-based computers via both trojanized software and various malware. Moreover, hackers promise to create personalized viruses to attack any given e-commerce entity.
On the one hand, e-merchants have to enhance their online activities to compete with rivals in the evolving online trade. On the other hand, a growing danger of cyber terrorism makes e-store owners think twice before launching new e-commerce projects. Since no anti-hacking panacea has been invented yet, the only right approach to the problem is the continuous improvement of cybersecurity literacy to address possible threats timely and effectively.
A professional e-store development vendor shares valuable cybersecurity insights in the post. Enjoy reading. Lets talk about it
Have a project in mind?
Fraud Economy Is Here to Stay
Hardly anyone knows exactly how large the total financial damage from cyberattacks is. Some experts feel that it is more appropriate to speak about a standalone type of economy that is emerging on our watch - the Fraud Economy. At least $1 trillion was lost by e-merchants last year globally due to cyberattacks. Some figures are shocking: malware cases increased by about 600%, for instance.
The landscape of hacking is too broad to leave any segment untouched. Besides e-shops, a lot of businesses are victimized: delivery services, crypto exchanges, tourism companies, entertainment providers, dating websites, etc. Nonetheless, e-commerce websites remain one of the most attractive targets for hackers. Certain considerations are available to explain why it is so:
- Private data. Usually, e-stores contain quite large databases with the personal info of customers. Hacking e-shop servers provides cybercriminals with a lot of valuable private data: names, addresses, phone numbers, emails, cloud profiles, corporate info, etc. Such data can be either sold in the illicit market or used to benefit directly when, for example, hackers obtain loans against the passport data of an unsuspected victim. However, cybercriminals utilize private data in a more sophisticated way most often. They crack passwords of users’ profiles to use legal accounts for malicious activities. They can sign up as a seller on a marketplace to offer nonexistent goods, for example. Consumers pay them money being unaware that the deal is fraudulent. It is extremely difficult to punish such hackers since the profiles are legally registered for law-abiding people who do not even know that their accounts are hacked.
- Online transactions. E-shops provide their users with opportunities to pay for goods online. Hackers can insert malicious codes into payment forms to hijack payments. Of course, the majority of the contemporary e-stores have implemented payment security standards such as PCI DSS to protect the banking cards of their customers. At the same time, attacks on databases are remaining dangerous.
The very e-commerce specificity implies that cybercriminals can potentially hack a network, a website, or a server with a DDoS attack, phishing, or other malicious methods (more on them later). Hence, e-shop owners should be able to recognize indications of every cybercrime to apply for support from cybersecurity experts in time.
.png)
Cyberthreat Modalities
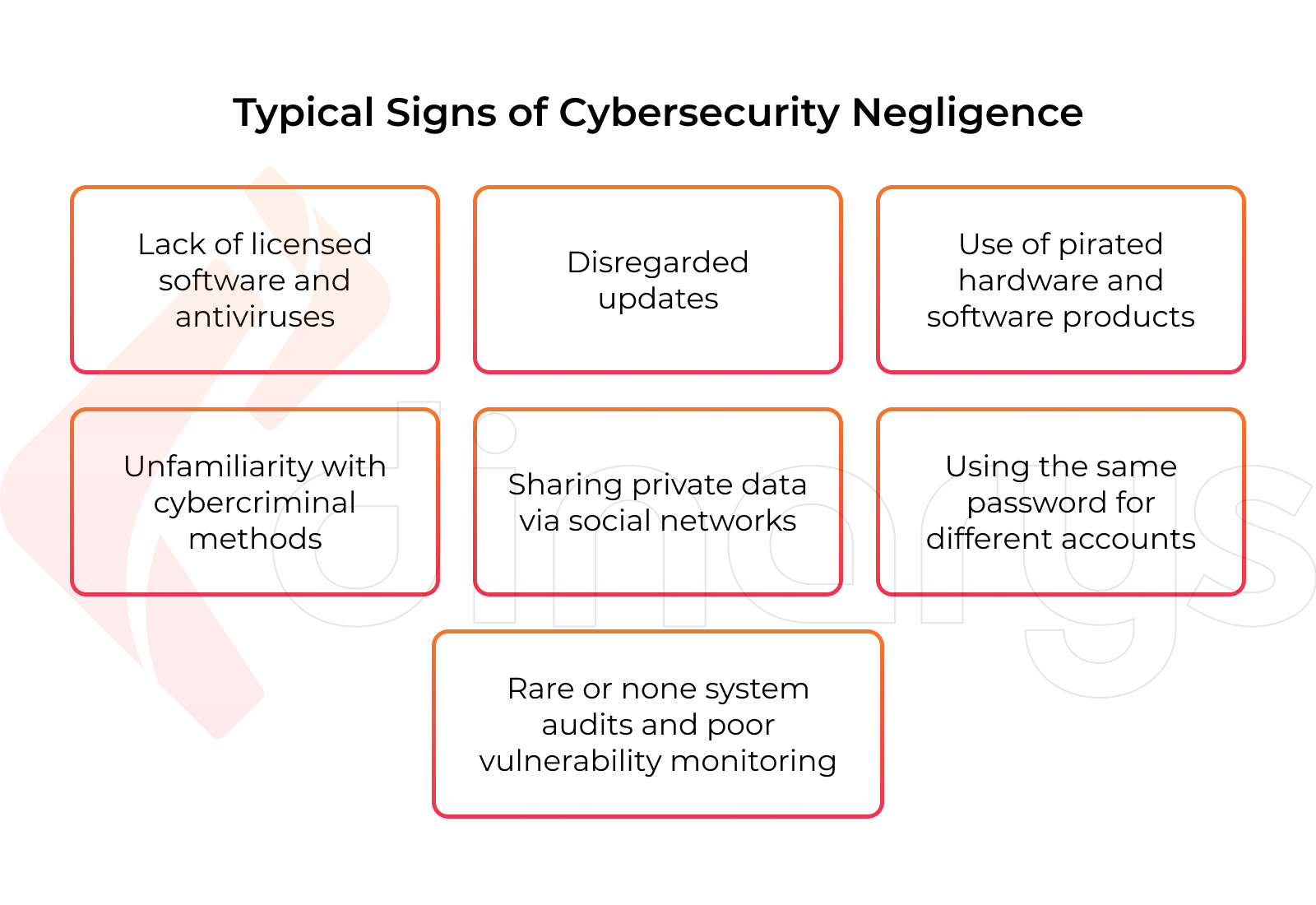
Viruses, ransomware, and other hacking tools are not the only causes that lead to the booming fraud economy. Oftentimes the wrong behavior of both e-shop owners and users helps hackers in their attacks. The most typical signs of cybersecurity negligence are the following:
- A lack of licensed software and antiviruses.
- Disregarded updates: security patches regularly released by software vendors are worth using to mitigate security vulnerabilities.
- Use of pirated hardware and software products.
- Unfamiliarity with cybercriminal methods: phishing, social engineering, and the like.
- Sharing passwords, usernames, and other private data via social networks where they can be easily intercepted by hackers.
- Using the same password for different online accounts when hacking a single profile provides access to all the others.
- Rare or no system audits along with poor vulnerability monitoring.
Being fully occupied by income-generating activities, many e-merchants tend to overlook their staff. Even a single poorly trained team member can put the entire enterprise at risk. Besides, the very access to commercial data can appear too tempting for people with low socioeconomic status. Something similar occurred at one New York-based company where an employee was trying to steal corporate revenue while getting access to a company’s server. As it was revealed, the company ignored penetration tests.
Security experts often repeat that the best way to protect your e-commerce project from cyberattacks is to prevent them. Even though many attacks are hardly trackable, the following symptoms can help realize that someone is trying to take over your website:
- IP address generates more queries than usual.
- It is technically possible to see that someone downloads new pages from your website every second.
- Glitches happen in your server from time to time.
- Your server delivers an error in response to a query.
E-commerce merchants should remember one simple thing about cybersecurity: the ones who do not care about their websites, servers, and networks are doomed to hacking at the end of the day.
Types of Сybercrime
The variety of cyberattacks is growing day by day since technical progress never stands still. At the same time, hackers are just humans who are oftentimes reluctant to try something new. They prefer using well-tested techniques in the hope that their victims are even more reluctant and ignorant about cybersecurity. Hence, the most popular types of cyberattacks are worth knowing.
1. Distributed Denial of Service (DDoS)
This attack is aimed at bringing a system to malfunction with an enormous amount of incoming requests. Cybercriminals send so many queries to a system that ordinary users cannot get through such a white noise.
Amazon was suffering just from DDoS in February 2020 when hackers were bombarding the platform with the flooding traffic of 2.3 terabytes/second. It took Amazon about 3 days to handle the attack.
The following recommendations can be useful to protect your e-commerce project from DDoS attacks:
- Regularly upgrade your server hardware.
- Maximally increase the number of connections to your database.
- Make your server withstand large traffic it is worth installing an open-source proxy manager such as NGINX.
- Install an additional interface that can be used when the main one appears overloaded.
- Never ignore updates and patches while using only licensed software.
- Use traffic analytics to recognize a DDoS attack coming.
- Protect your network servers with a firewall by providing only admins with access to them.
2. Phishing
This is a social engineering method when hackers pose as legal e-commerce entities. They are trying to ingratiate themselves with potential victims to get access to confidential info. Often cybercriminals prepare phishing campaigns in advance: they select a company, identify the company’s employees on social networks, monitor their activities, figure out what projects the company works over, etc.
After that, hackers create very personalized emails almost indistinguishable from the ones the selected company usually sends. As soon as a victim either open an attached file or follows a link, a virus appears in the victim’s computer. The following scenarios are possible when
- A phishing attack is ordered by a competitor, the received info can be used to destroy the company’s reputation.
- Important content can be blocked, and hackers can ask for a ransom.
The only way to avoid phishing is to always stay alert while working with emails, messages, and links. Besides, it is necessary to warn your staff about the JavaScript snippets that hackers can attach to drive you to fake websites where your payment data can be stolen.
Another popular phishing scenario relates to the popular payment system PayPal: hackers send a notification that your PayPal account is temporarily blocked due to suspicious activities. Instead of contacting the PayPal support team, users can input their login data to the delight of hackers.
Lets talk about itHave a project in mind?
3. Skimming
This is another type of cybercrime when hackers add virus code to several websites to collect the private data of users. They get access to web pages with payment forms and order confirmations. Emails, passwords, addresses, credit card numbers, and even CVV codes appear at their disposal as a result.
To minimize the danger from skimming e-merchants can do the following:
- If your e-shop is created with a free template, install a security plugin (Sucuri and the like).
- Protect your website with a firewall, use 2F authentication.
- Use a unique password that contains at least 10 symbols.
- Regularly update your system with new security patches.
4. Cross-site scripting (XSS)
In contrast to other types of cyberattacks, this one threatens shoppers rather than e-shops. XSS implies a virus code added to a web page. Usually, browsers do not recognize the code as a virus and execute it as a regular script. As a result, the script gets access to the cookies of end-users. Hackers receive confidential user info and utilize the users’ computers for their malicious activities via covertly installed malware (phishing emails distribution etc). The attack can destroy the e-store’s reputation since users tend to interrupt relations with the brand through which they have appeared victims.
To prevent XSS attacks the following is recommended:
- Both web and mobile versions of your e-store should have filters for all income data to know which info your users have access to.
- All variables should be encrypted before being sent to users.
- Delete all redundant data from your website such as HTML tags that can be dangerous.
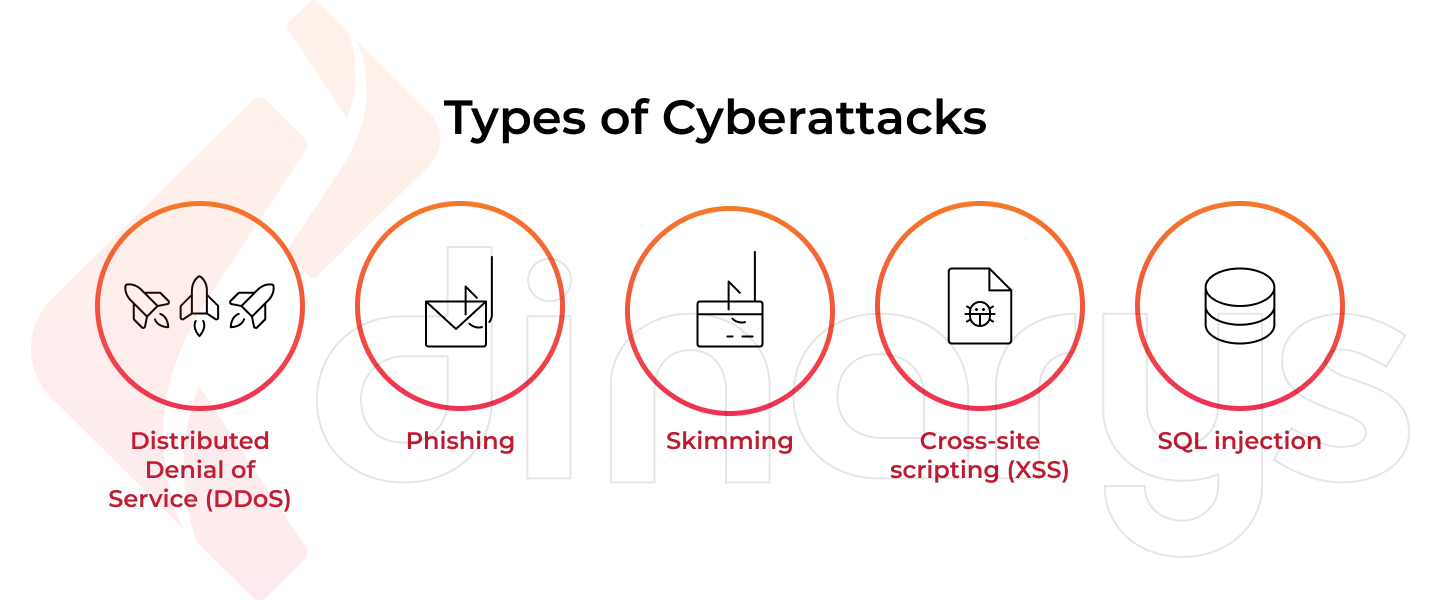
5. SQL injection
This is one of the easiest ways to penetrate a website that works with databases. The attack is based on adding arbitrary code to SQL queries. This helps hackers make an illegal query to a database to read tables, alter/delete data, etc. In doing so they get access to both private data of users and info about transactions. SQL injections allow hackers to circumvent authentication procedures on websites. Besides, hackers can encrypt databases to ask for a ransom for decryption.
There are some general suggestions on how to protect your e-store website from SQL injections:
- Use “white lists” for authentication forms when you indicate only allowed keys, variables, and symbols to exclude SQL injections.
- Instead of the GET method, use POST in the forms: GET sends unencrypted queries allowing hackers to know the variable names that can be used to make SQL injections.
- Establish a ban on processing internal/service files. All modules that can be plugged into your website (headers etc) should be collected to a special closed-access folder.
- Never make your website code publicly available. Even if you are looking for technical support from a coder community, use just a piece of code that needs to be improved.
- Never copy someone else’s code: it can be initially infected.
- Do not display errors on the already published website. They can be the food of thought for cybercriminals capable of understanding how to hack your website.
To learn more about the most common cybersecurity challenges, check out this video.
What Standards Help Improve E-commerce Security
It is not enough to have special security software with anti-hacking apps to effectively confront cyberattacks. Any e-commerce project should make its security policy adapted to the world cybersecurity standards such as PCI DSS.
Payment Card Industry Data Security Standard outlines the technical requirements that provide secure sharing of financial information when transferring funds. Any e-commerce organization that carries out online transactions should coordinate this activity with the following PCI DSS principles:
- A firewall to protect the data of cardholders must be deployed.
- No by-default passwords are allowed.
- Bank data of users should be encrypted before sending it via public networks.
- Install and regularly update antiviruses.
- Only responsible executives may have access to databases of customers.
- Everyone who has access to a corporate computer must be provided with a unique ID.
- Physical access to the bank data of customers should be reasonably limited.
- Access to both network resources and customers’ online banking must be continuously monitored.
- Regular vulnerability testing of the system is a must.
- The entire staff of your organization must be covered with a cybersecurity policy.
In addition to PCI DSS, companies that have sustainable e-commerce businesses should obtain ISO certificates. The International Standards Organization has developed special standards for e-commerce entities. The ISO/TC 321 standard, for instance, is aimed at the assurance of transaction processes in e-commerce. Compliance with ISO standards can significantly increase consumer confidence in an e-store that, in turn, can have a positive impact on its revenue.
Lets talk about itHave a project in mind?
Steps to Protect E-commerce Security
Unlikely a silver-bullet solution against cyberattacks can be invented anytime soon. The hackers vs e-merchants fight will continue with varying success most probably. However, monitoring suspicious activities on your e-commerce website along with clear awareness of cybersecurity approaches can protect your business against cyberattacks in most cases.
The following procedures constitute a compulsory checklist for e-store owners who care about their online security:
- Penetration tests along with vulnerability monitoring should be a regular practice to make sure your e-store protection against hacking is up to date.
- Always stay alert to recognize the slightest signs of any upcoming cyberattack. For example, when your website starts slowing down, neither cleaning cookies nor improving bandwidth makes sense since a DDoS attack seems going to happen.
- Never be tired to remind your staff that following unfamiliar links and opening attached files are dangerous: this is just the way viruses infect computers.
- Do not conduct transactions and send financial info via messengers when being connected to public Wi-Fi. If you have to do so, try to hide your geolocation and IP address with VPN and other means of confidential web surfing.
- Always monitor news about hacking novelties to be aware of what to expect. For example, ransomware is one of the most popular cyberthreats today when hackers encrypt your info to extort money for decryption.
- Implement additional identification factors wherever possible. Several technologies are available to arrange 2F authentication on your e-commerce website. Even if multi-factor verification adds inconvenience to your users, your cybersecurity is worth it.
- Hold private data of your customers separate from other information. Regularly make audits of your databases to figure out what data is redundant or obsolete.
- Deploy firewalls and arrange multi-level access to critical financial info. Assign roles to your staff to limit back-end access.
- Build your e-commerce business upon reliable platforms such as Magento and Shopware. Set up automatic updates, never ignore security patches especially when your e-store requires manual updates while running on the on-premise infrastructure.
- HTTPS hosting is a must for e-commerce websites today. It contributes a lot to both enhanced cybersecurity with SSL certificates and better rankings by search engines.
- Never try to save on security plugins and other tools that make your website less vulnerable to cyberattacks. Automate your protection with all available techs to decrease the impact of human factors.
- Care about regular backups of your databases and other critical content. Backup copies help quickly rebuild your website even if a fatal failure happens due to a successful cyberattack.
- Establish a strong partnership with software professionals to be always supported by their cybersecurity expertise. Rely on their knowledge of the best e-commerce platforms to make your online business sustainable growing.
Conclusion
E-commerce security has always been a multifaceted issue. And it will remain so in the foreseeable future. In attempts to earn easy money hackers will always be looking for vulnerabilities of e-commerce websites. In many cases, just the security ignorance of e-store owners helps cybercriminals do their dark undertakings.
Reliable SaaS e-commerce platforms with embedded cybersecurity tools provide the strongest foundation of any online business. Choosing such a platform must be the first step for any wise e-merchant. The second step comprises a whole number of easily graspable security practices that every far-sighted entrepreneur should always keep in mind to run a successful e-commerce business. The practices include both must-do and never-do things we have indicated in the present post.
Contact us today if you prefer focusing on commercial activities instead of being bothered with cybersecurity issues of your e-commerce business. We create invulnerable e-stores meeting the most advanced security techs and protocols. Reasonable pricing and fast time-to-market are always available as well.
FAQ
A reliable SaaS e-commerce platform is just the basis upon which a secure e-store can be built. After choosing the right platform, e-merchants have to acquire a set of rules and practices to protect their online businesses against cyberattacks. Some of the e-commerce security measures are simple and well-known (strong passwords, financial data encryption, VPNs and firewalls, etc). The other ones are more specific. It is better to select the platform whose embedded capabilities include the majority of compulsory e-commerce security techs and tools. Based upon our hands-on experience, we strongly recommend paying special attention to the leading e-commerce platforms Magento and Shopware.
A well-established e-commerce security policy must be created by every e-merchant as we believe. Full awareness of both possible cyberthreats and effective countermeasures is what can protect any e-commerce business from hacking. Cybersecurity literacy is not rocket science, every intelligent entrepreneur can grasp the main principles of doing online business securely. Besides, software professionals with strong expertise in e-commerce security are always to the rescue.
There are different types of cyberattacks. They have specific signs and reflections respectively. If your server is glitching while a website is slowing down, for example, it can be recognized as an indication of a DDoS attack. When you notice an unusually intensive activity on your website when new pages are downloaded every second, it also can be a sign that someone tries to take over your e-store. Not to guess about possible threats and vulnerabilities, we suggest establishing good cooperation with software professionals who can take charge of your e-commerce security.
Let professionals meet your challenge
Our certified specialists will find the most optimal solution for your business.