Content
DevOps Security Best Practices

Devops security ultimately allows enhancing standard in-house approaches to cybersecurity and other corporate risks. The improved protection is achieved by implementing and using confidentiality policies, management processes, tools, and governance structures to manage the DevOps environment management to improve the stability of business processes.
What is DevOps Security?
DevOps brings together development teams and security experts, testers. Based on continuous integration (CI/CD) and DevOps practices, the continuous deployment philosophy promotes faster, more flexible software release cycles, allowing you to replace large releases with regular updates.
This workflow format helps to maintain constant involvement of software developers in IT operations and promotes closer collaboration. The combined groups launch software and infrastructure with fewer errors that normally cause malfunctions, rollbacks. DevOps is a two-way approach that takes into account cultural change by transforming technology and tools.
Thus, figuring out DevOps security questions and implementing the respective practices, companies get the following benefits:
- standardization of release processes and infrastructure grants thorough system security;
- coding of cyclical commands provides end-to-end automation of processes, reducing manual tasks and human-factor risks;
- increased flexibility and quality of new updates and product releases.
Image Source: phoenixnap.com
Why security is important in DevOps
Security matters because it affects profits. Hacks and security breaches are backlash and customers need to know their information is safe if they want to be customers at all.
As impressive as the traditional DevOps approach is, introducing security into DevOps process chains can cause significant delays. Simply put, DevOps is too fast for traditional security. Manually assessing team ops security for vulnerabilities causes latency and ultimately slows down deployment.
SecOps was created in response to this. It follows principles similar to DevOps, combining two features to increase efficiency, awareness, and reliability.
What Does DevSecOps Stand For?
Providing DevOps security, it’s crucial to cover all stages of project development. A set of integrated security tools intended to protect every other element in the product life cycle (from the creation, deployment, testing, and release to support, maintenance, and updating) are collectively called DevSecOps.
In terms of this approach, special project management and cybersecurity features are implemented for all expert team members to use, such as:
- identity and access management (IaM);
- prioritization of user access and privileges;
- privation DevOps security, risk management;
- code analysis;
- configuration and vulnerability management.
One of the most relevant applications of such protection is the optimization of online stores’ operation, for which it is necessary to find a quality contractor. The team of specialists Dinarys has excellent development skills at Magento and in-depth BA expertise in eCommerce.
Also read: The Benefits of Magento Custom Module Development
DevOps vs DevSecOps
What is DevOps model?
DevOps is an approach to software development for creating flexible relationships between development and IT operations. Its goal is to enhance the organization's ability to deliver applications and services at a high speed. This approach in short lines has set the standard for the speed and quality of software development.
Prior to the launch of the DevOps model, development and operations ran in a siled model. However, in the DevOps model, both teams team up with engineers throughout the development lifecycle. Quality assurance teams are also integrated throughout the development lifecycle.
What is DevSecOps model?
DevSecOps is a logical development of existing DevOps practices characterized by the new vision of DevOps security tools, offering more than just another set of rules and regulations.
DevSecOps offers companies practicing DevOps progress in granting security quality, increased productivity, reduced compliance issues, and includes the following key features:
- adjustment of collaboration for achieving common goals by security experts based on business priorities;
- development and implementation of common methods - catalysts of product protection and success; creation of up-to-date audit logs;
- automation of recurring tasks for the organization of an interconnected flow of processes;
- implementation of preventive operational management tools;
- the use of operative information, process flow management, risk analysis based not only on code scanning;
- an automated DevOps security engineer that helps to minimize the human factor, allowing built-in response features to immediately redirect traffic, pause nodes for a further check, notify operators, and launch new instances;
- implementation of platforms that allow gaining all-around protection in a production environment;
- continuous testing to help identify issues on early stages and solve them with the least losses;
- public cloud containerization and automation methods to reliably and subsequently conduct a security audit, spending fewer efforts.
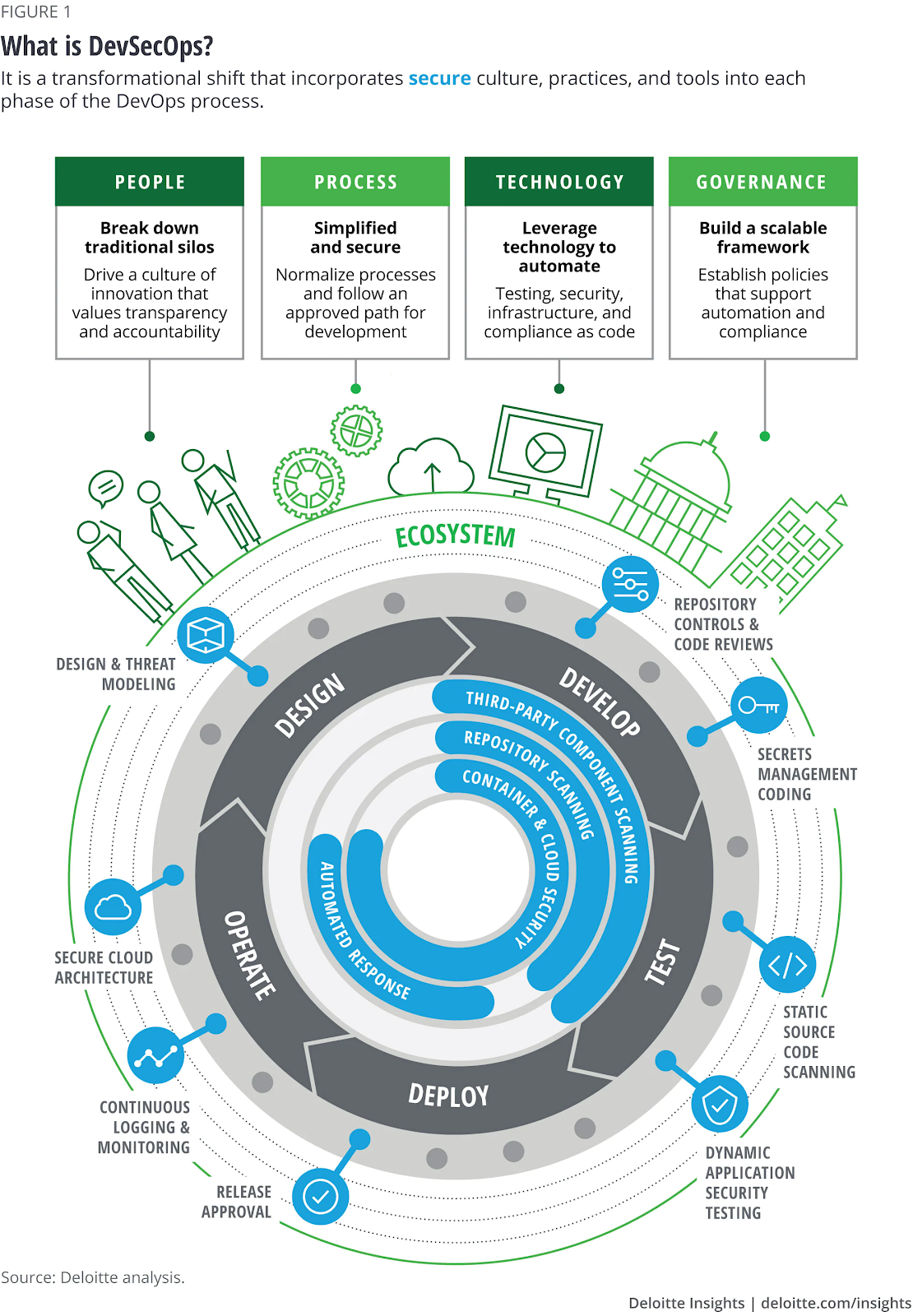
Image Source: www2.deloitte.com
Reasons to Employ DevSecOps
DevOps helps companies solve the issues of speed and flexibility, largely ignoring the problems of product protection.
DevOps security permissions are focused exactly on maintaining a security culture, ensuring the safety of data and prevention of mass leakage, minimizing the cost of further elimination of negative consequences. A properly built protection system includes the following key elements:
- customizable security rules - this allows defining the best security solutions in the process of planning and software coding. Operative groups can then promote the most efficient methods and procedures;
- natural protection - implemented in the early stages, DevSecOps make all-around security an essential part of the whole project life cycle.
- regular automated checks - employed in every other part of edited code, they help to reduce testing time as well as general expenses.
Learn more: How to Reduce and Manage Cloud Costs
DevOps Security Best Practices
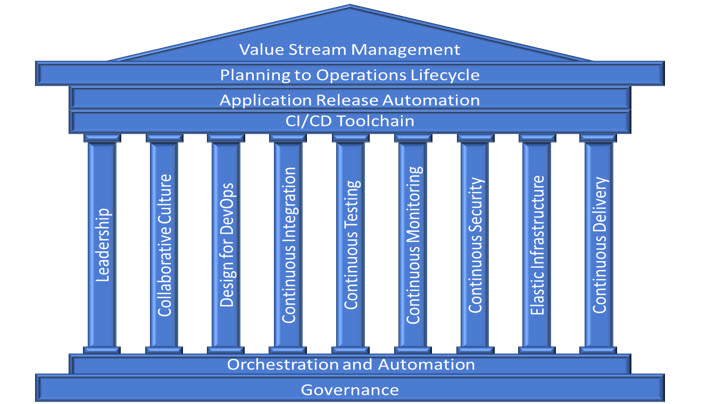
Image Source: devops.com
Management
In their managing practice, project leaders should:
- have a tactical, strategic understanding of security development goals (at least three years ahead);
- stimulate team growth - keep in tune with the progress, the question used methods, boost skills (e.g., via DevOps security certification courses).
Collaborative culture
Coming up with a universal goal for organization, team, which includes overcoming security issues:
- encouragement of inter-functional cooperation;
- check of security toolsets by experts;
- assignment of personal responsibilities.
Design
Mastering advanced security methods:
- check of source code edits via up-to-date tools;
- analysis of components for flaws and vulnerabilities;
- inspection of security carcasses and protective coding.
Continuous integration (CI)
A complex but utterly necessary process in organizations where several teams work based on different workflow schemes:
- incremental static analysis before verification and confirmation is tied to CI;
- binary artifacts are stored in safe storage;
- software version management system is used for managing versions of all edits in source code.
Continuous testing
Implementation and compliance with advanced security methods:
- automated tests selected for every other version by default;
- the creation of new tests according to particular code that are integrated with a branch highway;
- implementation of modular, functional, and integration trials;
- dynamic, interactive checks for vulnerabilities.
Continuous monitoring
Consideration of the dynamic properties of artifacts and infrastructure:
- a volume of security defects identified before implementation;
- a number of failed builds.
Continuous protection
A generalized security foundation that is based on the top practices:
- integration of security tools in the CI/CD chain;
- external penetration testing;
- telemetry;
- making source code available only to verified users;
- inventorying of all software packages.
Resilient infrastructure
Provides dynamic properties instead of static and requires:
- automated checks;
- IaaS or PaaS elements that are checked in accordance with business requirements;
- lowered complexity of workflow due to a fewer number of clusters.
Continuous product delivery/deployment
Minimization of risks based on:
- compliance with particular indicators before release;
- white list for app segmentation;
- security checks and requirement compliance based on the continuous deployment processes.
DevOps Security Automation
Organizations that combine IT operations, security groups, and application developers are required to integrate respective protection in their workflow chains. It should be a key component of the workflow and not a constant adaptation at the end of the cycle.
DevOps provides a delivery speed that should not be leveled out by adding security. Automated controls in the early stages of the development cycle ensure the fast delivery of your applications. One of the common methods of protection is code analysis.
Azure DevOps security scanning
It is a set of automatically loaded tasks for launching safe development tools in the assembly pipeline, which consists of:
- Login data scanner - a static analysis tool that helps identify confidential data in the source code as well as in the final builds;
- BinSkim - a lightweight scanner that checks compiler and assembler configurations;
- TSLint - an expandable part of static analysis that checks the code for readability, servicing, and functionality errors;
- Analysis and processing of security results;
- Security issue reports.
ТОР-5 DevOps Security Trends
Each year, the common understanding of DevOps deepens, leading to new methods, tools, and processes for bringing developers and IT operations closer together. Consider the main trends that will be most relevant in 2020.
A deeper understanding of the DevOps methodology
IT developers and experts already realize the difference between an isolated DevOps team and a collaborative approach to the development, deployment, and operational life cycles. Engineers learn to specialize in their field, while at the same time building a broad understanding of the rest of their applications, which leads to faster development processes and increased project sustainability.
Custom roles & responsibilities
Cybersecurity professionals need a broader understanding of the business in addition to their technical capabilities. Companies closely monitor in-house processes and employees to establish corporate qualifications and the availability of everything necessary to fulfill major functions.
Growth of cloud computing, storing, & implementing
DevOps developers increasingly shift towards the cloud to facilitate rapid changes in the production environment, improve the transparency of all applications and infrastructure, creating sustainable architecture. Cloud architectures (based on AWS, Azure or GCP) turn platforms and features into easy-to-use services (FaaS, PaaS, IaaS).
Image Source: victorops.com
Symbiosis SRE & DevOps
Engineers combine DevOps and Site Reliability Engineering (SRE), recognizing the value of both. DevOps - a methodology for closer collaboration between developers, SRE - specific technical experience. In 2020, the active integration of SRE and DevOps continues to create sustainable continuous deployment pipelines.
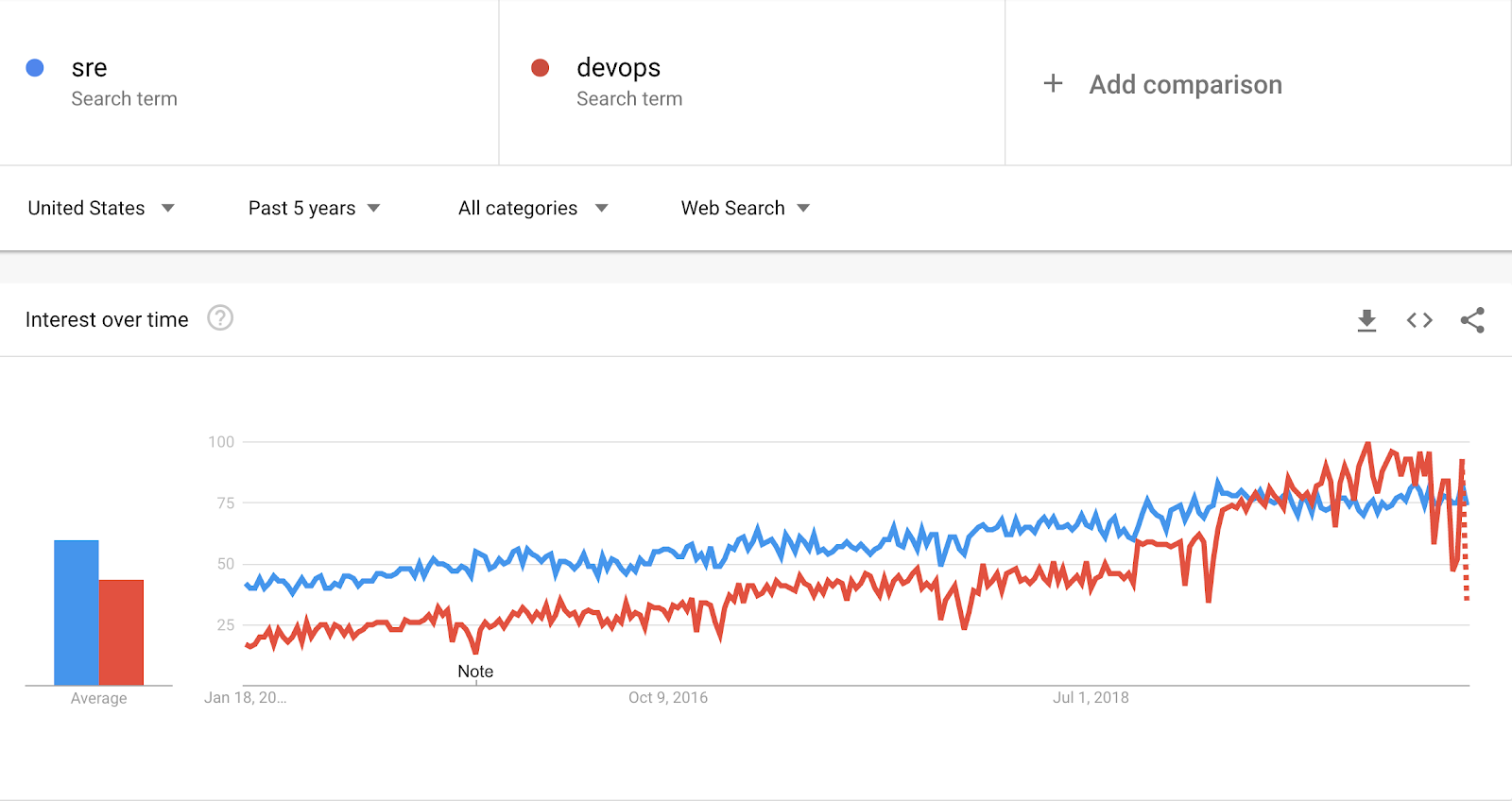
Image Source: victorops.com
Standardization of CI/CD
Google Trends engineering teams are starting to see CI/CD as a requirement. More and more people understand the difference between CI, CD, and other CDs, using them as a competitive advantage for fast customer service. A well-built CI/CD pipeline improves speed by helping to increase the overall reliability of supported services.
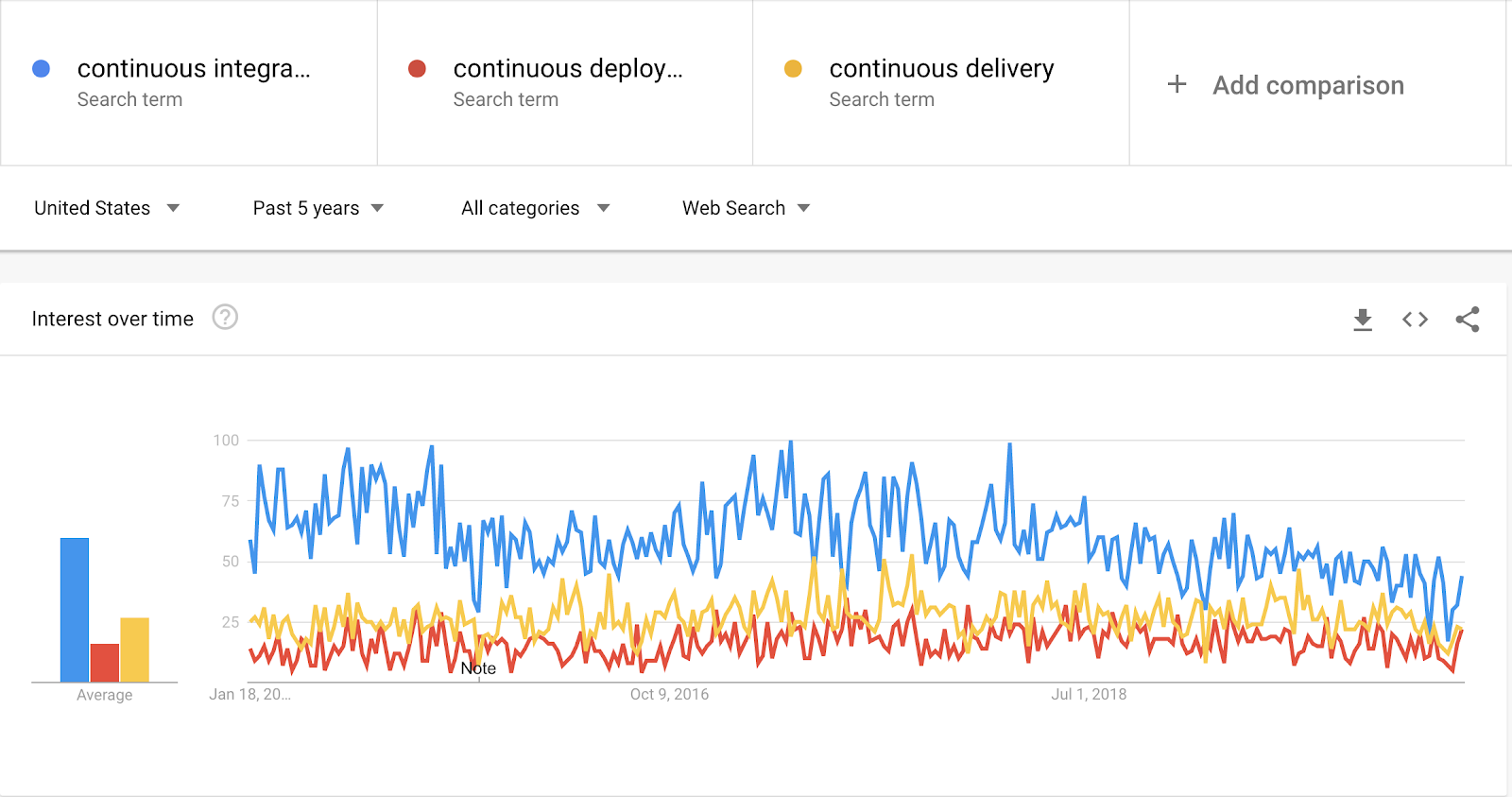
Image Source: victorops.com
Be one step ahead of your competitors - turn to our team of DevOps experts right now! We provide specialized consultations and help in building all-around protected software systems.
Summary
The degree of security of the final product is no less important than its quality, since the inability to fully place, store information in it also significantly affects the functionality.
Both modern security and hacking technologies never stand still, dictating more and more new development trends. It is not enough to check the final security of the product - it is important to control this process at all stages of development. That is why DevSecOps comes to replace DevOps as a logical, relevant continuation of evolution.
Lassen Sie Profis Ihre Herausforderung meistern
Unsere zertifizierten Spezialisten finden die optimale Lösung für Ihr Unternehmen.




